Data Protection Tips
This article covers data protection tips and data recovery tips.
Protection of data revolves around three main areas of business practice - prevention practices, recovery strategies, and offsite storage considerations. Let's review all three to better understand the role each plays in the overall protection scenario.
Data Protection Tips for Prevention Practices:
Everyone who uses a Personal Computer (PC) is susceptible to data loss. Many of us will experience some type of data loss in the not too distant future. It may be a single file or the whole hard drive. By understanding the likely causes of data loss, we can take precautions and reduce the risk.
According to Disaster Recovery Trade Journals, data loss is the result of the following types of occurrences:
- 44% - Mechanical failures, such as drives, heads, and power.
- 32% - Human error, including accidental deletions, spilled drinks, and not shutting down the system properly.
- 14% - Software problems, which occur when software revisions aren't properly tested.
- 7% - Viruses.
- 3% - Natural disasters, such as hurricanes, tornadoes, and lightning strikes.
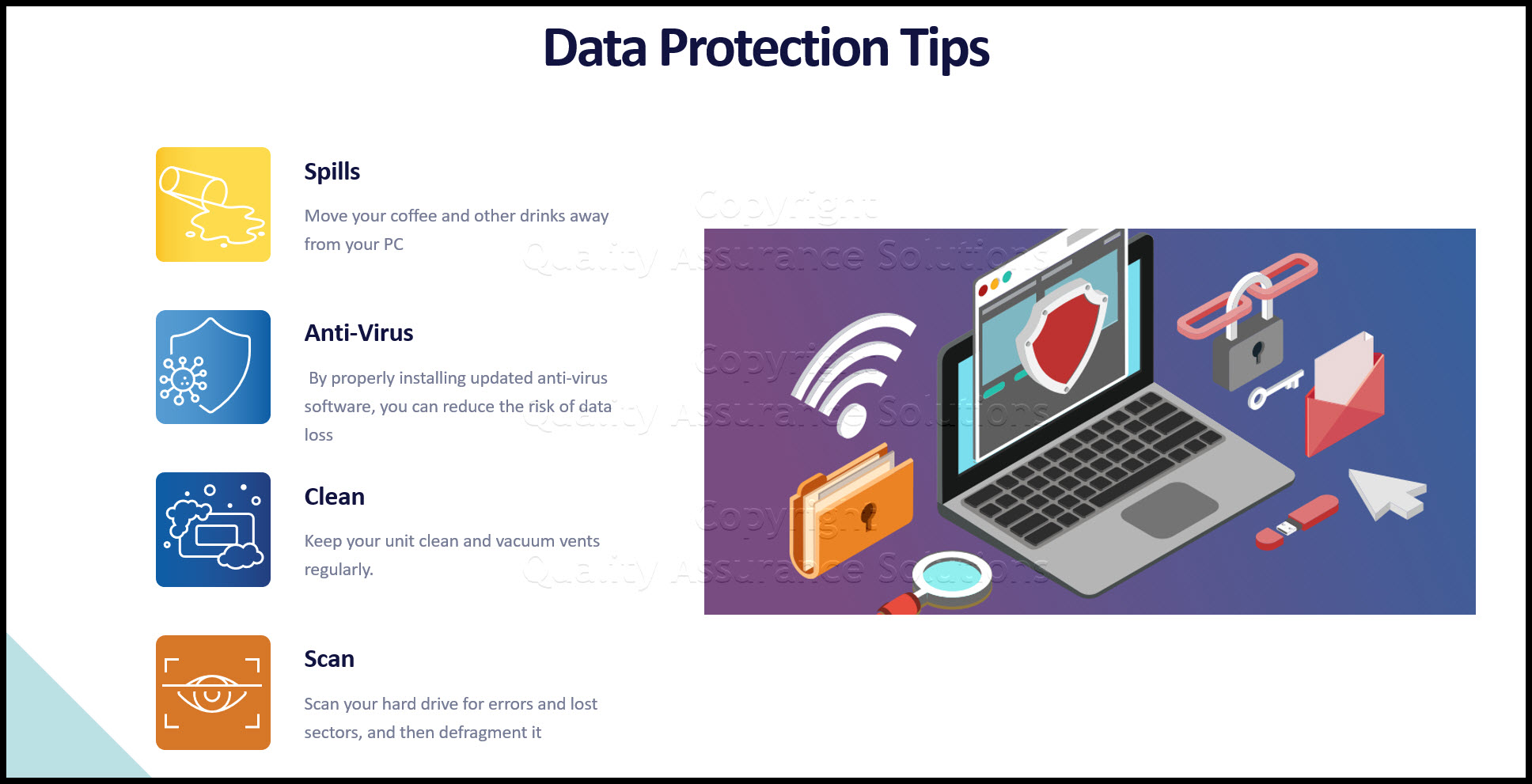
Let's look at some practical data protection tips you can take to reduce the likelihood of data loss.
- Move your coffee and other drinks away from your PC. Spilled drinks cause more than just sticky keys; they are a formula for data loss.
- Use a recommended anti-virus software package. By properly installing updated anti-virus software, you can reduce the risk of data loss by some bit-eating virus, worm, or Trojan-Horse.
- Never connect or disconnect cables or peripherals when your system is on. Power off your unit completely.
- Keep your unit clean and vacuum vents regularly. Dust particles have been known to cause system crashes.
- Scan your hard drive for errors and lost sectors, and then defragment it. (Not necessary for SSD drives). Utilize common system utility programs that comes with most PC's to butt used disk space together and unused (free) disk space together to enhance system performance, while lessening data loss risk. Do at least once a year and only after doing a complete, tested backup.
You won't completely stop data loss from occurring, but by reducing the risk and having a complete, tested backup, you can minimize your exposure and protect your data.
8D Manager Software with 8D, 9D, 5Y and 4M report generator. Your corrective action software for managing, measuring, and reporting issues.
Data Protection Tips for Recovery Strategies:
Data Recovery Strategy sounds very impressive, but not really all that involved. It's all about backing up data, storage of the backups, and then being able to utilize them to do a restore / recovery. Various categories of computer information require a data recovery strategy which may or may not be the same.
These categories include:
- Operating System Environment
- Application Support Software
- Customer Data
- Company Data
Data recovery strategies require plans for backup, off-site storage, and data recovery.
You should consider two aspects of backup. One is a disaster recovery backup where you store backup copies are in a facility considerably removed from the primary computer center. The other is an operational recovery backup where you retain backup copies on the premises to accommodate many possible operational situations.
Note these data protection tips for your company's backup...
- Creating and labeling daily, weekly, and/or monthly backups of pertinent information, based on how difficult it might be to recover / re-create, can save hours of heartache, at a minimum.
- The time to create a backup copy can range from five minutes to many hours depending on the size of the system or set of information you desire to back up. Always identify the contents, the date of the backup, and the data classification.
- When you develop backup and recovery plans, you should consider the different processing requirements that may exist between normal processing and disaster situations.
Other factors to consider include:
- What to backup
- How often to backup
- When and where a backup is stored
- How to identify and retrieve a backup
- How long to keep a backup
- What to do with the backup at the end of the retention period
- What storage media to employ
- Who is responsible for execution
- Who is authorized for backup and recovery
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
Data Protection Tips for Offsite Storage:
If you ask most people to show you their PC backups, they reach for their desk drawer, that is if they have any at all.
Off-site storage keep the data safe and as a protective measure away from the primary location. Then, if a disaster destroys the primary location, then the off-site storage location makes the data available for recovery.
Data protection tips for arranging for business off-site storage involves the following:
• Select an off-site storage facility.
• Establish procedures to manage and control the rotation of backups to and from the off-site storage facility.
• Move backups off-site following a planned schedule.
Follow these guidelines for quality off-site storage:
1.) Identify an off-site facility that has the following characteristics:
- Separate location from the primary location (it is recommended that the location be at least 25 miles away) to prevent a disaster from affecting both sites.
- Controls for temperature, humidity, and fire protection.
- Accessible 24 hours a day, 7 days a week to authorized personnel.
- Secure access controls.
- Capability to rotate backups to both primary and alternate processing locations.
- Bonded employees.
- Electrical power backup.
2.) Document the following:
- Methods for identifying disaster recovery backups.
- Method for transportation to the storage facility.
- Process for rotation / retention.
- Personnel that have authorized access.
- Obligations for nondisclosure of backup data.
- Shipping and receiving schedules.
- Length of storage contracts.
- Cancellation provisions.
3.) Define procedures to be followed at the off-site storage facility during normal, non-disaster periods.
4.) Define procedures to be followed at the off-site storage facility during a recovery operation.
Equally important is having good backup procedures. They essentially ensure that you capture critical company, customer data, and personal data. Make it everyone responsibility to backup data necessary for the recovery of their job functions. This is critical for Knowledge Management in your Quality Management System.
Listed below are some items to consider backing up and moving to an off-site location:
• Personal files containing critical data.
• Phone lists (customers, employees, vendors).
• Financial documents.
• Any documents or manuals necessary to perform your job.
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
Data Protection Tips for Contingency Plan
Data protection tips include including data recovery in your contingency plan. Since the 9/11/2001 terrorist actions, Business Continuity and Disaster Recovery place more prominent in chief executive officer planning strategies. In addition to terrorist threats, weather happens. Occurrences like hurricanes, tornadoes, spring storms, summer heat, autumn winds, floods, fires, and winter freezes always lurk around the corner.
The most important step in dealing with a disasterdevelop , you must develop plan in advance. Immediately on the heels of developing the plan, you must test it.
The Disaster Recovery Plan (DRP) ensures that, when the unexpected happens, the business, division, department, site, or individual can continue to do business smoothly (business continuity), with minimum disruption to normal operations. Unfortunately, the unexpected happens more often than some might think.
As a business issue, contingency management needs to be addressed through a well-defined and thoroughly tested DRP. The plan must be built on an examination of all categories of risk that can be reasonably anticipated. The plan must cover all aspects of concern to the business: its staff, its customers, its suppliers, and its assets.
Company's managers must have a well-defined, tested plan to execute if disaster strikes; while each employee's must be prepared for and respond to a disaster in a professional manner.
Many of us think that management handles disaster recovery planning for us. However, the individual employee's must do his or her part, such as backing up that critical data on personal computers on a frequency commensurate with its sensitivity / criticality, and storing back-up media off-site, etc..
As we become more and more dependent on desktop computer power as well as local and wide-area networks, the company places more and more responsibility on the individual to have an individual plan that dovetails with the higher-level business units plan, or site plan.
We usually think of disasters as major fires, earthquakes, hurricanes, tornadoes, and floods, but disasters can begin very small and become catastrophic by our own failure to properly prepare.
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |