IT Audit Program
Key Elements
The IT Audit Program key elements documented here comes from an audit compliance, or auditors perspective. If you implement an IT Audit Program, you will enable great results that follow with fewer (maybe zero) information security incidents, and fewer (maybe zero) audit comments written during an external IT audit.
Background
An effective Information Security Program includes awareness, education, training, policies, procedures, controls, reviews, and especially, separation of responsibilities. However, good Information Security Practices require more than correct practices to be effective. They must have real and continued management backing and involvement.
Management must be pro-active regarding Information Security Practices. They must let their people know it's important through example. They must take pride in their program. They must help bring about attitudinal changes in their people through;
- strongly administered security awareness programs
- bringing about a clear understanding of the reasoning behind Information Security Practices;
- instilling real concern about Information Security
- instilling dissatisfaction with anything less than great Information Security.
Executive management must apprised newly appointed management detail of the company's information security practices, and annually refresh existing management too.
In addition, to be successful with Information Security Practices and pass an IT Audit Program, management must also organize their team with clearly defined roles and responsibilities, with no conflicts of interest. Separation of responsibilities must be an integral part of Information Security. Training must be provided as required.
8D Manager Software with 8D, 9D, 5Y and 4M report generator. Your corrective action software for managing, measuring, and reporting issues.
Note: Proof must be produced during an IT Audit Program to substantiate ones practices. Archive audit documentation a minimum of six-months.
Further, management must also learn to manage "smarter". The multitude of information security practices required to address the major concerns and issues, and the associated workload to do so, mandates that management be imaginative in administering the responsibilities to put these practices initially in place, and keep them in place on an ongoing basis.
IT Audit Program Current Situation Assessment
- IT Audit Program consistently turn up fundamental Information Security violations.
- Managers do not consistently promote or enforce good Information Security practices in their work groups.
- Employees do not view software copyright violations as serious offenses.
- Employees are not aware of the Information Security issues related to networks.
- Viruses are an increasing threat to company computing systems.
- Employees do not consistently backup and place offsite their work to facilitate recovery in the event of a disaster.
- Crisis and Contingency Management plans are not consistently in place across the entire company.
- Employees do not view telecommunication fraud or misuse as serious offenses.
- Distributed processing lacks the same level of controls that exist in mainframe environments.
- Increased "hacking".
- Increased theft of laptops.
- Increase of widespread disasters such as earthquakes, floods, fires.
- No consistency of Contingency Management plans across all platforms.
- No consistent Information Security Awareness Program across the Company's Business Entities.
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
High Level Needs Determination
A robust Information Security Awareness Program will always support Corporate IT Policy and organizational goals and objectives:
- Corporate IT Policy will state the need for Information Security Awareness, and if it doesn't, it should.
- In general, most IT Audit Program looks at an Information Security Awareness Program as being visible with surface proof that management is concerned, the business is controlled, information is adequately protected, and laws are not being violated.
- The value can be articulated to leadership in terms of their objectives.
- The results can anticipate and satisfy company and customer unspoken needs.
Organizational Needs Identification
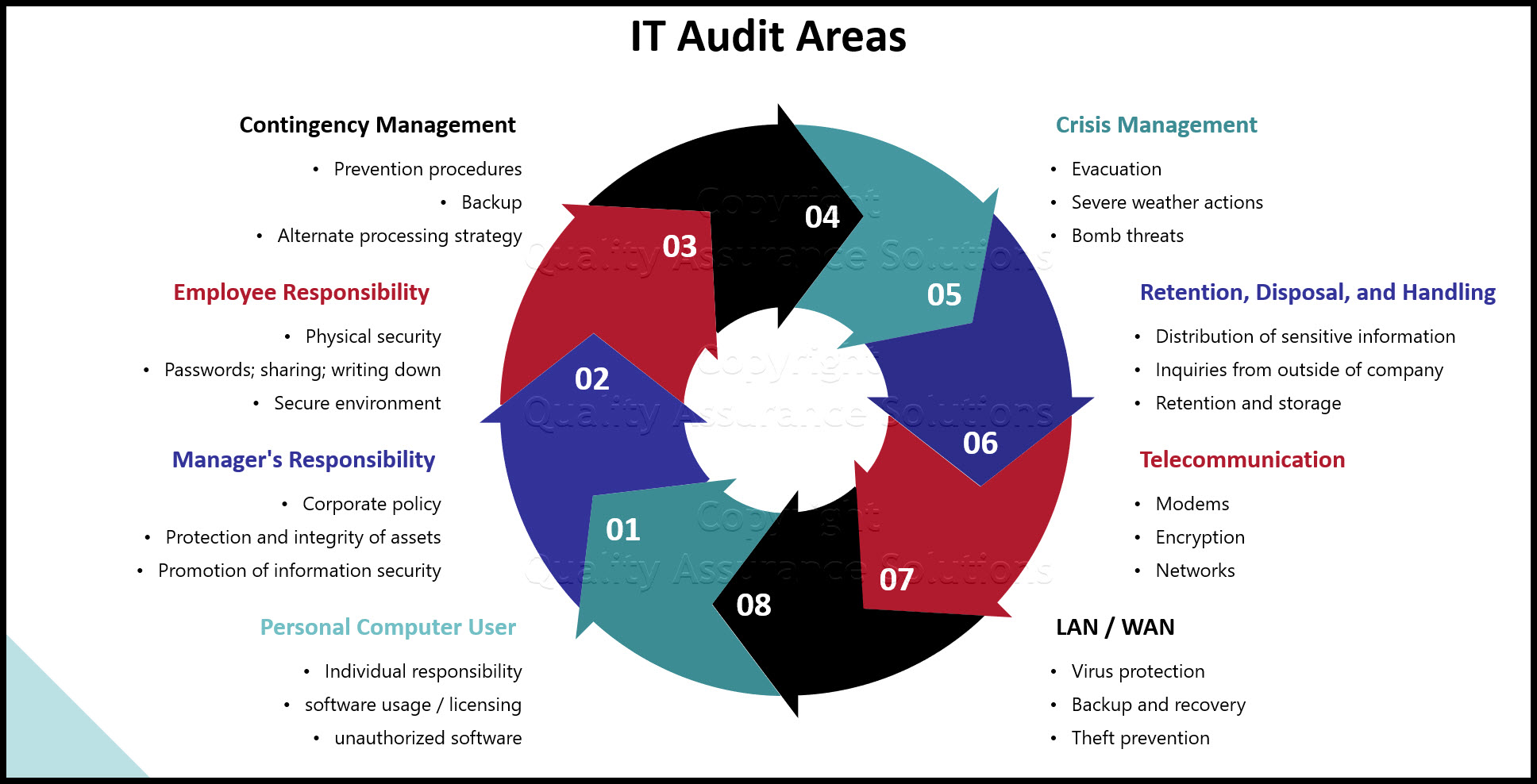
Personal Computer User Issues:
- Corporate policy
- Individual responsibility
- Software usage / licensing concerns
- Unauthorized software
- Back-ups
- CD / USB / SD and other media security
- Practice and risks of exchanging media between work and home
- Virus protection
- Business / non-business use
- Housekeeping
- Physical protection
- Failing to logoff
- Risks to system
Get certified in Risk Management through our completely on-line training system. Study at your own pace.
Manager's Responsibility Issues:
- Corporate policy
- Protection and integrity of assets under their control
- Promotion of Information Security
- Review and resolve unauthorized access violations
- Investigate and correct exposures
- Notification of personnel transfers and terminations
- Material disposal
- Segregation of duties
- Secure the environment
- Provide customer support
- Perform random reviews of employee activity
- Control of corporate resources
- Ensure compliance to corporate policy
- Authorize access and review privileges
- Compliance with security policy
- Compliance with business continuity policy
- Compliance with network access policy
Employee Responsibility Issues:
- Corporate policy
- Individual responsibility
- Ethical responsibility
- Compliance with corporate and local policies
- Material disposal
- Protection and integrity of assets under their control
- Passwords; sharing; writing down
- Secure environment
- Business continuity
- Physical security
- Knowledge of customer information
- Clean desk practice
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
Contingency Management Issues:
- Corporate policy
- Individual responsibility
- Customer service level requirements
- Prevention procedures
- Backup, off-site storage, and recovery
- Alternate processing strategy
- Network recovery strategy
- Documenting disaster recovery plans
- Customer reaction plan
- Disaster recovery plan testing
- Continuous improvement process
Crisis Management Issues:
- Corporate policy
- Individual responsibility
- Evacuation
- Severe weather actions
- Bomb threats
- What to do; where to go; who to contact
Retention, Disposal, and Handling Issues:
- Corporate policy
- Individual responsibility
- Identifying sensitive information
- Classifying sensitive information - company
- Classifying sensitive information - customer
- Printing sensitive information
- Faxing sensitive information
- Voice transmissions
- Distribution of sensitive information
- Inquiries from outside of company
- Retention and storage of sensitive information
- Reproduction of sensitive information
- Disposal of sensitive information
Get Green Belt Certified with this extensive on-line course. Learn the Six Sigma tools and steps. Earn 25 PMI PDU. Start implementing Six Sigma today
Telecommunication Issues:
- Corporate policy
- Individual responsibility
- Disaster recovery
- Modems
- Encryption
- Networks
- PBX toll fraud
- Cellular phones
- Travel call cards
- Awareness
- Voice mail protection
LAN / WAN Issues:
- Corporate policy
- Individual responsibility
- Virus protection
- Backup and recovery
- Theft prevention
- Copyrights and licensing
- Secure data
- Password standards
- Housekeeping practices
- Policy and procedures
- Client server risks
- Dialup access controls
- Modems
Get certified in Risk Management through our completely on-line training system. Study at your own pace.
Risk Identification
The IT Audit Program identifies potential risks to your business and your customers' business exist if no formal Information Security Awareness Program exists. You may not know about or be able to comply with corporate policies, procedures, and sound business practices, potentially resulting in the following:
- Poor audit compliance reports; in addition to loose security, this is usually a career limiting event
- Loss of customer confidence in your business
- Increased risk of loss of customer information
- Risk to information integrity
- Risk to information confidentiality
- Risk to information availability
- Increased vulnerability to theft
- Increased vulnerability to unauthorized access
- Increased risk to personal / physical safety
- Unpreparedness for a disaster
Some areas of vulnerability or risk associated with Information Security are:
- Ethical practices
- Computer viruses
- Personal safety
- Software piracy
- Handling of sensitive information
- PC security practices
- Building access
- Telecommunications fraud
- Leadership example / practices
- Crisis management
- Contingency management
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
Value Determination
An Information Security Awareness and an IT Audit Program enables your business to accomplish the following:
- Improve the morale of employees by providing them with information they need to perform their jobs effectively.
- Present Information Security issues to the company leadership on a consistent basis so that Information Security is identified as important and integral to the way you do business.
- Help to ensure good audit reports by providing employees with knowledge on Information Security issues.
- Strengthen the relationship with your customer by reinforcing good Information Security practices.
- Make employees aware of their responsibilities.
- Help to ensure the protection of information / assets.
- Help to ensure timely recovery in the event of a disaster.
Legal and other Requirements
Federal
- ANTITRUST LAWS - May not share competitively sensitive information with competitors about prices, future product plans, marketing strategies, etc.
- FOREIGN CORRUPT PRACTICES ACT (FCPA) - Makes all managers and directors personally liable for the protection of company assets under their control, specifically information.
- COPYRIGHT LAWS - Copying of copyrighted software must be in strict compliance with all appropriate licensing agreements.
State:
Generally speaking, these laws make it illegal to attempt an unauthorized access or assist in an unauthorized access of a computer system.
Corporate Requirement:
Employees must understand the requirements of the Corporate IT Policy.
Your ISO 9001:2015 Kit includes Templates, QA Manual, Implementation Guide and a Gap Assessment Internal Audit Tool for ISO 9001:2015
Manager Requirements
- corporate policy - company and customer
- individual responsibility / liability
- responsibility for the protection and integrity of assets under their control
- responsibility to promote Information Security Awareness
- obligation to see that unauthorized access violation reports are reviewed and resolved
- obligation to investigate and correct known exposures
- responsibility to ensure that information security personnel are expeditiously informed of all personnel transfers and terminations in order to remove system access privileges
- responsibility to ensure that material is disposed of properly
- responsibility to incorporate the segregation of duties concept where it makes good business sense
- responsibility to ensure that the overall work environment is secure, and that information is protected during all phases of testing, and that the test and production environments are kept separate
- perform periodic random reviews of employee activities and datasets to act as a deterrent against non-business use of company resources
- responsible for compliance with all corporate policy, especially Information Security and Business Continuity
Employee Requirements
Employees need to know:
- Sensitive information handling practices
- Ethical responsibility
- Individual responsibility
- Evacuation plans
- Severe weather actions
- Off-site usage of computer resources
- Proper PC backup procedures
- Voice mail protection
- Etc.
Customer Requirements
Employees must be aware of customer policies and requirements for handling of customer data.
Audit Requirements
Employees must be aware of and exercise proper information handling procedures.
Your company can address all of the issues surfaced during an IT Audit Program through a robust Information Security Awareness Program. These are all real business issues that any legitimate business would take action to address - action begins with AWARENESS.
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |