How to Protect Against Phishing
Companies that protect against phishing attacks fortunately don’t make the news, because they prevent a big problem. According to the 2018 Small Business Cyber Risk Report from Hiscox, 47 percent of small businesses suffered a cyber attack in the previous 12 months. The worst part? Cyber-attackers hit most businesses more than once.
Clearly, small businesses don't take the appropriate steps to protect against phishing. Plus, they don't and respond like they should when cyber attacks happen. But why?
We see that business's owners understand the risk: 66 percent responded that they’re concerned or very concerned about cyber attacks. However, half of businesses owners cite finances as the reason for not taking a proactive stance against cyber attacks. Those executives miss one key fact: Human error, not infrastructure, causes their greatest vulnerability.
To protect against phishing, business owners can invest in cyber insurance, install intrusion detection, and / or hire cybersecurity experts, but without addressing the human element of cybersecurity, their efforts fall short.
That’s especially true for phishing scams, a type of social engineering attack that continues to grow in prevalence as internet users’ trust in the digital world increases. Kaspersky Lab’s Spam and Phishing Report found that phishing attacks among their users grew dramatically in 2018, with a 27.5 percent growth between Q2 and Q3 alone.
Your ISO 9001:2015 Kit includes Templates, QA Manual, Implementation Guide and a Gap Assessment Internal Audit Tool for ISO 9001:2015
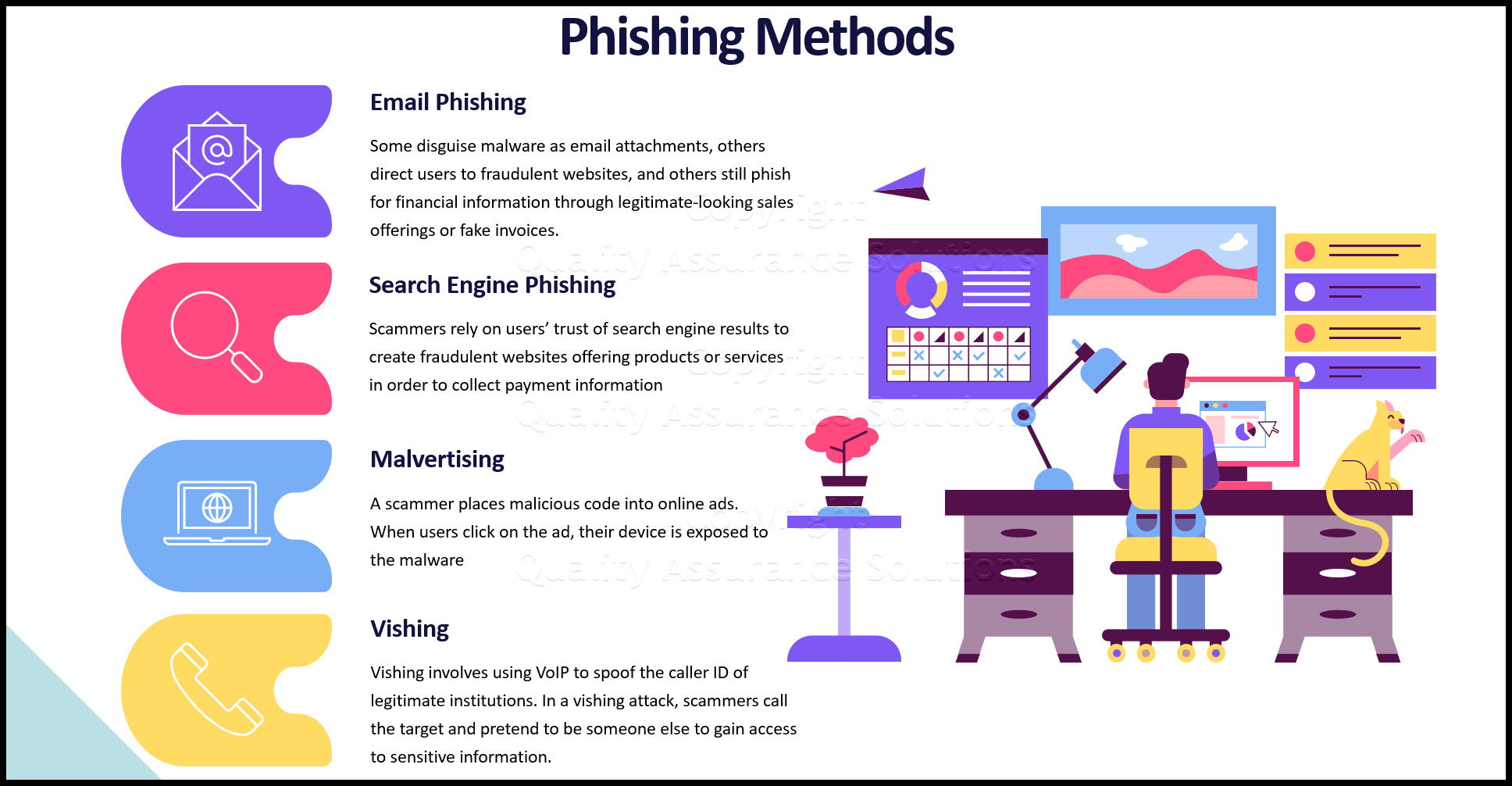
Most Common Phishing Scams
Email phishing
Email attacks come in several forms. Some disguise malware as email attachments, others direct users to fraudulent websites, and others still phish for financial information through legitimate-looking sales offerings or fake invoices. Many email phishing scams use current events to gain the users’ trust; in 2017 and 2018, scammers used cryptocurrency, EU General Data Protection Regulation, and the World Cup to grab users’ attention.
Search engine phishing
With search engine phishing, scammers rely on users’ trust of search engine results to create fraudulent websites offering products or services in order to collect payment information. The phishers then drain users’ bank accounts and / or steal their identities.
Malvertising
For malvertising, or malicious advertising, a scammer places malicious code into online ads. When users click on the ad, their device is exposed to the malware
Vishing
Vishing involves using VoIP to spoof the caller ID of legitimate institutions like banks, police, or even the IRS. In a vishing attack, scammers call the target and pretend to be someone else to gain access to sensitive information.
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
How to Protect Against Phishing Attacks
Business owners can’t stop every phishing attack from reaching their employees, but they can avoid becoming a victim. Doing so requires a two-pronged approach:
- Employee Training
- Security Policies
Invest in employee training. It only takes one mistake by one employee to cost a business tens of thousands of dollars. Business owners must train employees to detect social engineering attacks and keep their staff up-to-date on new scams.
Your company can easily set security policies, but make sure you enforce them too. Instead of asking employees to create difficult passwords and change them regularly, use a password management program that gives employees no choice but to follow password protocol.
You can also hire a professional hacker to test the strength of your network and identify and address any problem areas. You can find qualified hackers through freelance job boards and choose a candidate based on their rate and reviews.
Business owners should also restrict an employee’s ability to use personal devices over business WiFi. While a bring your own device policy may seem harmless and financially prudent on the surface, it causes a major security threat to small businesses. Additionally, the use of endpoint detection and response software, which monitors activity on a network and records that info into a database, can also protect sensitive data.
Article written by Dean Burgess of Excitepreneur.net for Quality Assurance Solutions. Article edited and posted by Quality Assurance Solutions.
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |