Prevent Scary Emails
Equipment and information, including scary emails, in any form is considered an asset of the company and thus must be properly used and adequately protected. This includes the transmission of information over computer communication networks.
Electronic mail systems are a company resource that without policy and sound business practice, could experience severe trauma resulting in deteriorating message delivery and response time or, even worse, system unavailability.
Special note and refrain should be paid to the circulation of chain letters. This activity causes a dramatic increase in the allocation of disk space to user data, a dramatic increase in the likelihood of a computer virus, worm, or Trojan Horse attack, and places a strain on resources that could result in extended outages.
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
Email Retention
E-mail and other forms of electronic communication, like any other written communication, can be subject to subpoena. Corporate management faces a difficult tasks to controlling scary emails . To make Electronic Mail management even more complex, companies should tightly-couple it with document retention.
Mostly e-mail is good! First, retained e-mail enables a company to respond to any client request or issue after a project has commenced or completed. Second, in the event of a dispute with a customer, vendor, or other third party, a company must be able to defend itself and prove what it did on the project and how it complied with its duties or obligations. Thus, if the e-mail / document in question is necessary to any of these purposes, it should be retained.
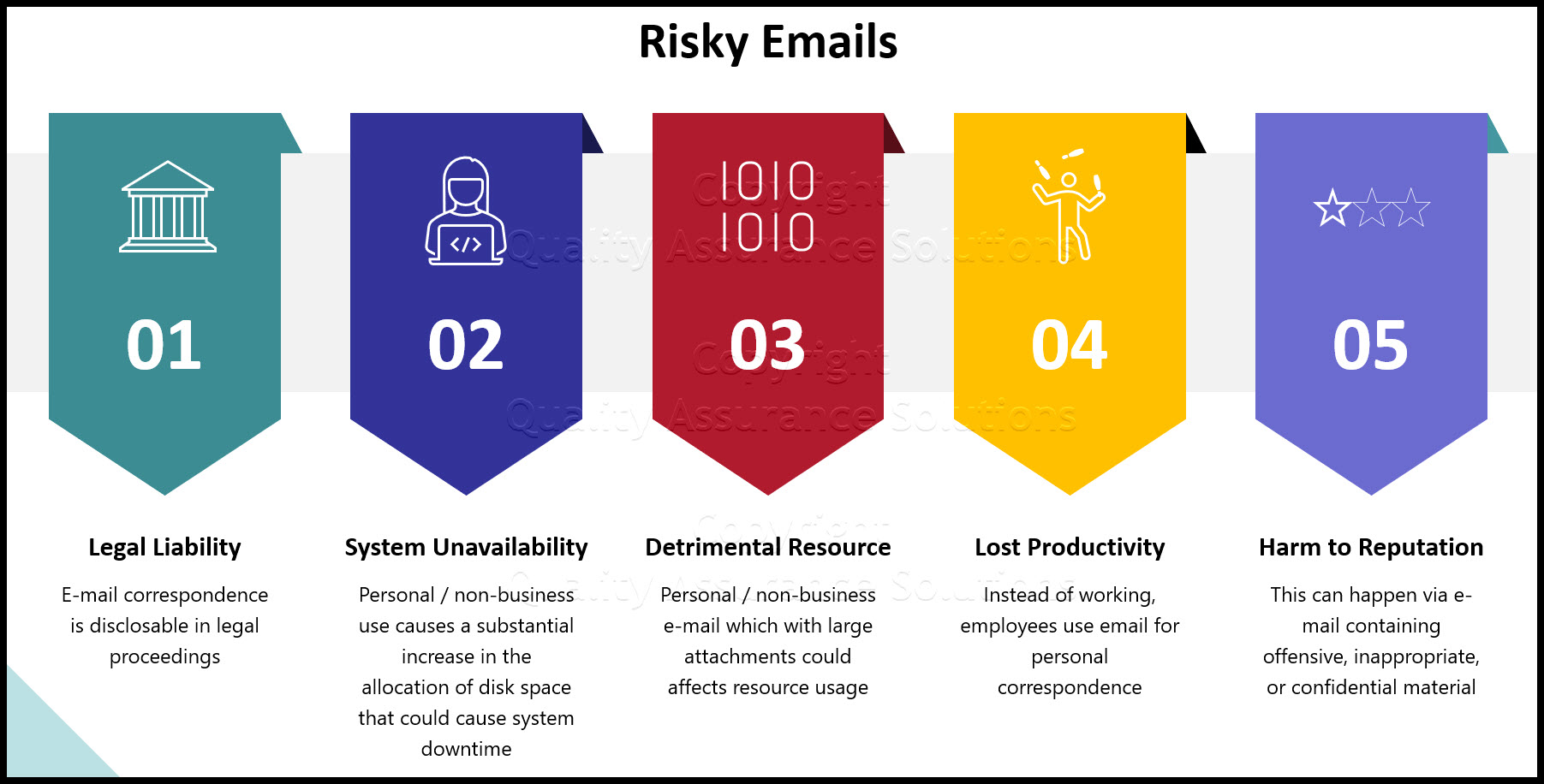
Scary Emails Risk
Following is a quick summary of some of them:
Legal Liability - As mentioned already, e-mail correspondence is disclosable in legal proceedings. To have a leg to stand on at all, companys need to, at a minimum, publish guidelines regarding the usage of their company provided electronic mail systems. If not, usually it's employers rather than employees who are held legally responsible for the contents of messages, and any associated viruses transmitted from their e-mail systems.
System Unavailability - Personal / non-business use causes a substantial increase in the allocation of disk space to user data, a dramatic increase in the likelihood of a computer virus, worm, or Trojan Horse attack, and places a strain on resources that could result in deteriorating message delivery and response time or, even worse, system unavailability.
Detrimental Resource Usage - Personal / non-business e-mail which quite often contain large attachments, e.g., videos, pictures, etc. use substantial network bandwidth and disk space, which results in a reduced availability of these resources for business related needs.
Lost Productivity - A significant amount of e-mail handled by a company’s electronic mail system is not of a business nature. Surveys indicate that the majority of employees use company provided electronic mail systems for personal correspondence. This also has an impact on mail server performance and space utilization.
Harm to Reputation - This can happen via e-mail containing offensive, inappropriate, or confidential material.Confidentiality Violations - This can include the divulging of closely guarded company information, e.g., the company's strategic direction, new product plans,other internal information, etc. This could happen accidentally or on purpose.
8D Manager Software with 8D, 9D, 5Y and 4M report generator. Your corrective action software for managing, measuring, and reporting issues.
Email Policy
You can manage the above noted risks formally by publishing policy (policy can be easily formulated from these guidelines). Following are some of the positives that can begin to result from publishing your Electronic Mail Guidelines:
- Greatly improved Electronic Mail usage focus
- Fewer Electronic Mail incidents
- Reduced legal risk
- Fewer audit concerns / comments
- Delivery of best practice information to employees
- Greatly improved business focus
SPAM - Junk E-Mail
If your mailbox at home is anything like mine, you go through the daily ritual of filing / flinging your junk mail in the trash. Junk mail has become a common practice in our society. If you have a mailbox registered with the United States Postal Service (which most U.S. residents do) then you've received unsolicited mail.
But can scary emails junk be sent to your e-mail address, and if so, where does it come from, can it be stopped, and should you report it to someone?
Let's look at these questions one at a time, starting with the first. Can junk mail be sent to my e-mail address? The answer is yes. Many of us, especially those with access to the Internet, have experienced junk mail in one form or another. We've seen it as: "Money-Making Blockbuster"; "It's Your Turn to Win"; and the most common come-on, "Forward This to All Your Friends".
But where does it come from? Most of it originates from the Internet, and it's the electronic equivalent of junk mail.
This type of scary emails has been given the name "spam" by the e-mail community, and the senders of unsolicited e-mail are known as "spammers".
Note: spam is not an acronym. It is a slang name for Unsolicited Commercial E-mail (UCE).
Spam basically involves sending scary emails to large lists of people with no previous relationships. The e-mail addresses may have been "harvested" from dark web, forums and member directories, classified ads, public newsgroups, etc.
Spam or unsolicited e-mail is enormous in volume (number of messages). Estimates vary widely, but calculations indicate that 30% of all e-mail is unsolicited.
Well, what's the problem. Just delete it, right? Wrong. Scary emails costs the sender next to nothing. However, that does not make it free. The messages have to be carried. One of the largest expenses that Internet Service Providers (ISPs) face is telecommunication bandwidth. If they are carrying a lot of junk mail, they (and us) are paying for it.
It also clogs the overall system, making it slower for everyone involved. It costs the recipient, who opens and usually reads whatever it is before clicking-on delete. Estimates of the value of the loss of time run into many, many hours and hundreds of dollars a year per employee or other measure.
Many organizations have been hit with spam attacks causing deteriorating system resources and productivity, as well as embarrassment for some when the subject was of a sensitive nature.
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
Can't spam be filtered? In theory, yes, but in practice, not really.
Spammers constantly find new ways of hiding their addresses, disguising their messages, and otherwise evading anti-spam technology.
One favorite method of penetration is deliberately misspelling key words, like "Viag*a", "gi*ls", "sin*les", and "d*et," so as not to invoke automated spam removal software.
Another is offering unwitting consumers an "unsubscribe" link. If you click on it, you only confirm that your e-mail address is active. This information is then sold to other spammers.
A Harris Poll found that 74 percent of Internet users want spam banned outright, with only 12 percent opposed. Eighty percent said they found spam "very annoying."
Not surprisingly, anti-spam groups flourish. One of the biggest is Spamhaus of Great Britain, which issues "blacklists" of fraudulent spammers and alerts their service providers in order to attempt to get their accounts cancelled.
Can scary emails be stopped? Probably not, but you can reduce the spread of spam (pardon the pun).
First, never reply back to a spammed message. Doing so lets the sender know that the e-mail address is valid, and more valuable for future mailings.
Second, when using the Internet, be cautious to whom you give your e-mail address to. Many spammers purchase large lists of e-mail addresses from other companies on the Internet. Third, never forward spam messages throughout your organization. Become part of the solution, don't become a spammer yourself.
Who can I report a spam attack to? Well, in most cases a single spammed message should just be deleted without any further investment of time.
But, if you and/or your organization repeatedly receive scary emails from the same entity, you can report the spammer to one of the many spam watchdog groups available on the Internet. They dedicate themselves to stamping out unsolicited commercial e-mail, newsgroup spamming, and other forms of scary emails abuse. They'd be glad to hear from you. They also provide instructions on how to filter e-mail, defend a site from exploitation, and get involved in the fight against spammers.
Get certified in Risk Management through our completely on-line training system. Study at your own pace.
CAN-SPAM Antispam Bill
CAN-SPAM appears to be a compromise that's not as far-reaching as some antispam advocates had urged. It does allow the Federal Trade Commission to establish a "do not spam" registry, overrides many state laws, and imposes an "opt out" standard instead of a more stringent "opt in" requirement.
The final bill says spammers may send as many "commercial electronic mail messages" as they like as long as the messages are obviously advertisements with a valid U.S. postal address or P.O. Box, and an unsubscribe link at the bottom. Junk e-mail essentially would be treated like junk postal mail, with nonfraudulent e-mail legalized until the recipient chooses to unsubscribe.
Other sections of the bill prohibit the following:
- Falsifying e-mail header information or using either a mail server or open relay to "deceive or mislead recipients" about the origin of a commercial e-mail message. Also outlawed is registering for "5 or more" e-mail accounts or "2 or more domain names" with false information and using them to send commercial e-mail messages. Penalties include up to three years in prison for a first offense.
- Sending commercial scary emails with deceptive subject lines that "would be likely to mislead a recipient."
- Sending commercial e-mail that does not include "a functioning return" address or a link to a Web form that is capable of accepting unsubscribe requests.
- E-mail address "harvesting" by crawling Web sites, and automated guessing of e-mail addresses by trying mike1@hotmail.com, mike2@hotmail.com, etc.
- Using automated methods such as scripts to sign up for free Web-based e-mail accounts such as ones provided by Hotmail or Yahoo.
- Sending scary emails with "sexually oriented material" unless it includes a label to be devised by the FTC. That requirement does not apply to opt-in lists. Violations can be punished by up to five years in prison and a $250,000 fine.
Your ISO 9001:2015 Kit includes Templates, QA Manual, Implementation Guide and a Gap Assessment Internal Audit Tool for ISO 9001:2015
Email Chain Letters
Chain letters continue to be an ongoing concern throughout most companies and organizations. Participation in the distribution of chain letters is a personal decision, but it SHOULD NOT occur as a business expense to one's company.
It is a misuse of company resources to use inter-office mail, electronic mail, or any other means of business communication to initiate or continue the sharing of a chain letter. Chain letters can slow down the delivery of pertinent business documents by creating downtime or slowdowns in electronic mail systems or creating excess letters in company mail-rooms.
Electronic forwarding of scary emails causes a dramatic increase in the allocation of disk space to user data, a dramatic increase in the likelihood of a computer virus attack, and places a strain on company resources that could result in deteriorating message delivery and response time or, even worse, system unavailability.
In addition, the use of computing and technology investments should be for legitimate company business purposes except for personal use deviations approved by one's department head. If you have any questions or concerns regarding chain letters, please contact a member of your management team.
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |