Biometric Verification
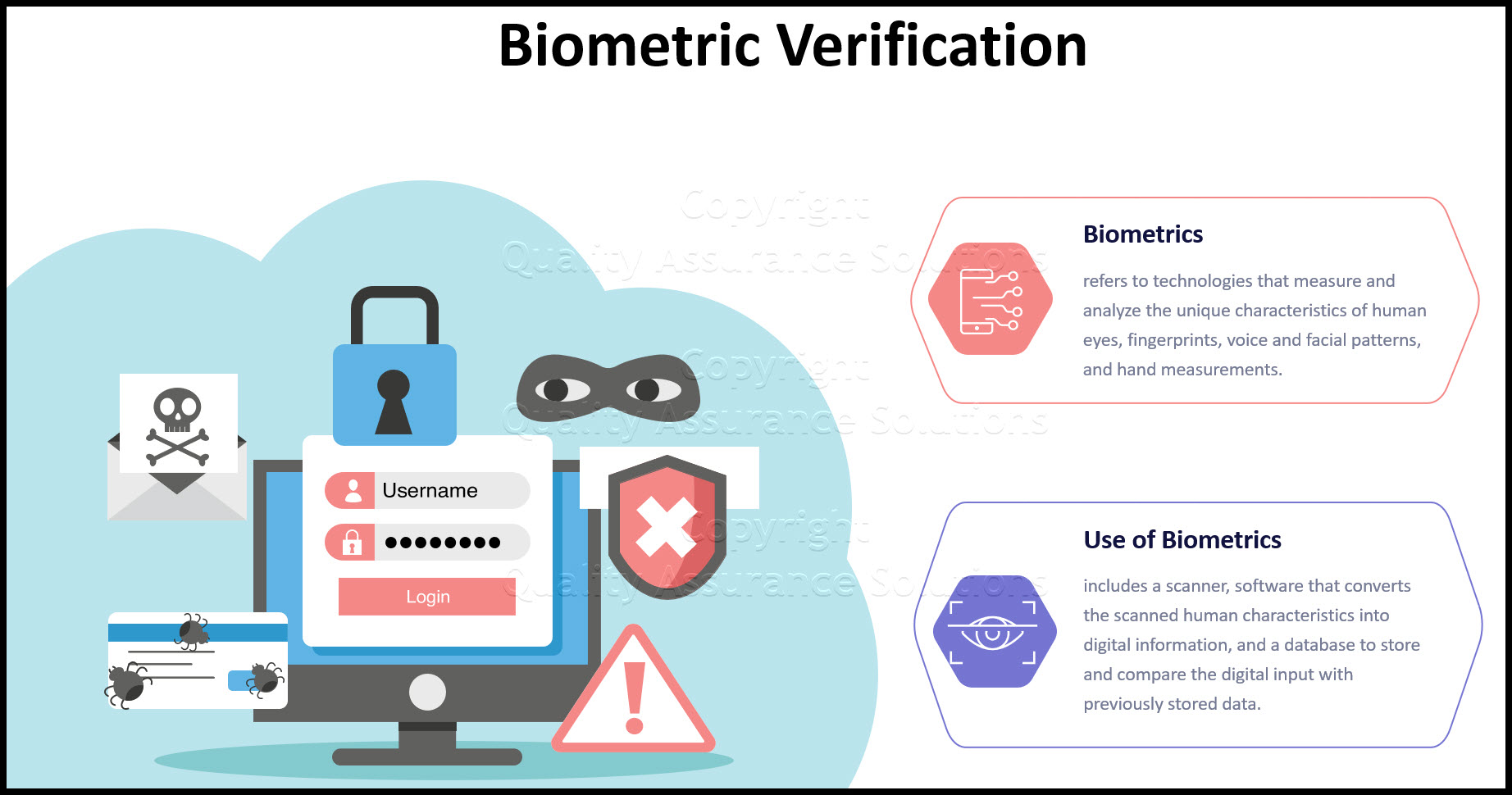
Today and in the distant future biometric verification technology can provide passwords to your computer, bank, and other systems and transactions that require user identification and authentication access controls to protect against unauthorized access.
Biometrics generally refers to technologies that measure and analyze the unique characteristics of human eyes, fingerprints, voice and facial patterns, and hand measurements.
The actual business use of biometrics includes a scanner, software that converts the scanned human characteristics into digital information, and a database to store and compare the digital input with previously stored data.
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
Current industry standards support identification codes and passwords to prevent unauthorized access to information, although other technologies, such as smart cards or biometric verification are used to manage access to highly sensitive information.
The September 11, 2001 terrorist attacks created a renewed sense of urgency regarding all security matters, and gave biometrics an added lift. In addition, biometrics are getting closer to widespread implementation as the price falls and the practicality rises while businesses continue to try to eliminate non-value added costs associated with processes required to address things like forgotten passwords.
Cost of Lost Passwords vs Biometric Verification
It has been estimated that every time a computer user calls the help desk for assistance because of a forgotten password, it costs one's company upwards of $50. Biometric systems are tightly-coupled to a single person, and cannot be easily used by an imposter. This provides a significantly higher-level of user authentication assurance over traditional signatures, passwords, and smart cards that could be used by someone who found one of these laying around.
Estimates are that the use of biometrics will grow more than 50% a year for the next five years by the need for faster, more secure, easier ways to access both data and physical space. So until you are affected, continue to practice good password habits:
• at least 8 characters
• combination of numbers and letters; not easily guessed
• not the same as your user id
• change it every 30 days
• don't write it down
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |