Software Installation and Upgrade Process
Important Steps!
Each year, businesses across the board spend
an average of around 8.2% of their revenue on IT. Your
company’s technology is a huge component of your success. However, if you’re not a
tech guru yourself, you may be intimidated at the thought of completing an unfamiliar software installation and upgrade process. Don’t let fears hold your company
back from the success and follow the below steps.
Two Types of Software to Consider
If you’re not sure where, exactly, to channel your information technology dollars, consider project management and ERP.
- Project Management. MS Outlook helps you with individual tasks to track and complete
- Enterprise Resource Planning. Enterprise
resource planning is crucial to your bookkeeping efforts. As your company
continues to expand, you need to take steps to ensure your finances stay
balanced. For this, you’ll need the right software. One example of business software for your enterprise is the
aptly named FractionERP. Although it operates much like a large ERP,
it’s more affordable and easier to learn. The program tracks stock, balances workflow, and manages purchases.
8D Manager Software with 8D, 9D, 5Y and 4M report generator. Your corrective action software for managing, measuring, and reporting issues.
Why Upgrade Your Business’s Software?
There are many reasons that updating your company’s software is a smart idea. First is security. Updated software combats the most-recent threats. Next is usability and features. Unless you frequently update or upgrade your software, you may miss out on important features that boost efficiency and productivity. Furthermore, if your business maintains compliance with regulatory boards, new software helps you do this. These are just a few of the most important reasons cited by AZ Big Media.
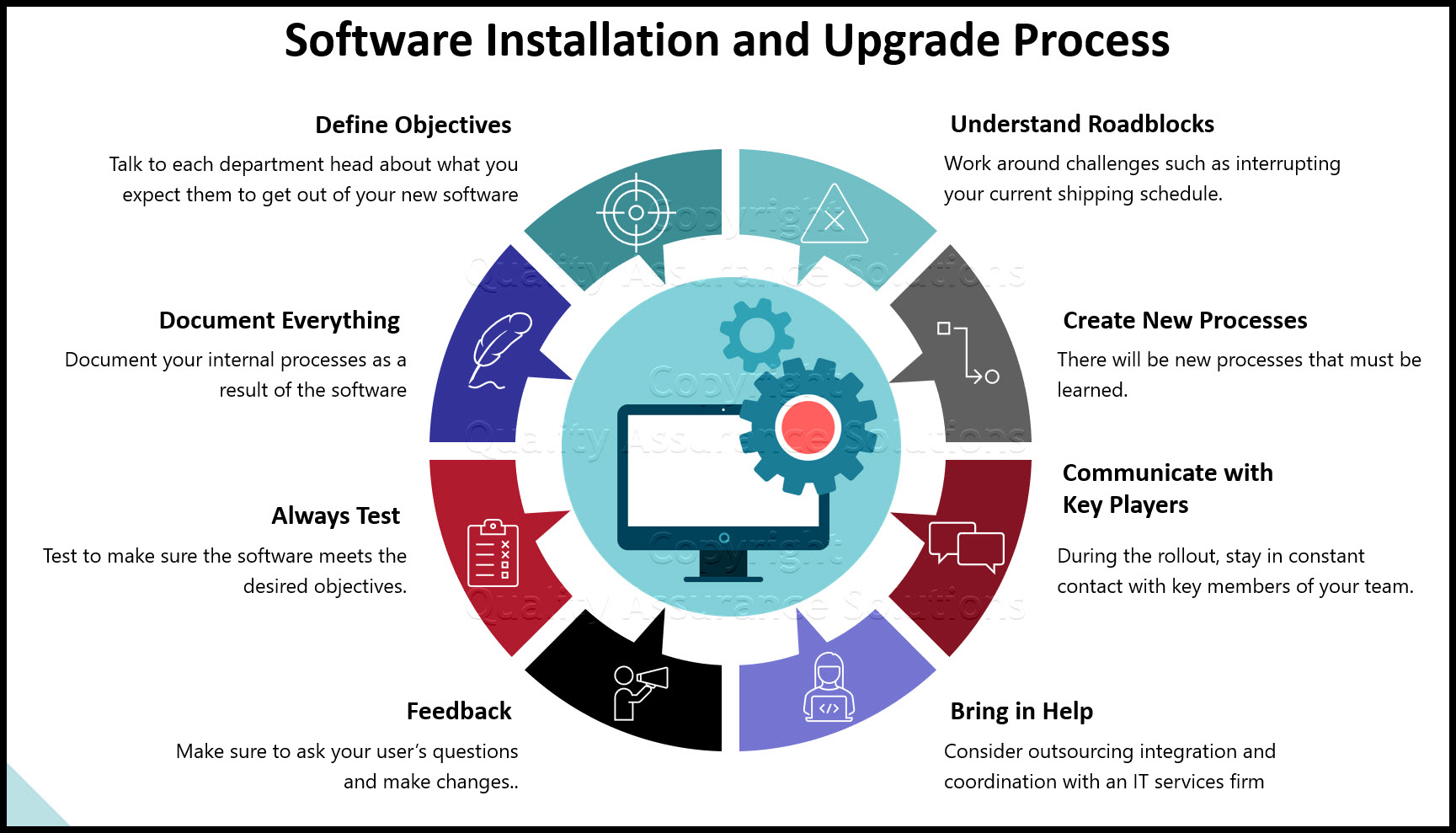
Software Installation and Upgrade Process
Knowing what type of software you want for your business determines only half the battle. You also need to plan ahead if you want a successful release. Your software installation and upgrade process should include these steps:
- Define objectives by department. Talk to each department head about what you expect them to get out of your new software. Give them clear objectives so that they know exactly what to look for in the new program.
- Understand roadblocks. The software installation and upgrade process doesn't always go smoothly. Work around challenges such as interrupting your current shipping schedule.
- Create new processes, and train your employees in them. Very rarely does the newly installed software allow you to run your business the same
exact way as before. There will be new processes that must be learned. Know
these early on. Then train your employees on how to best implement
your new programs. Training is a priority.
- Communicate with key players. Communication is essential throughout the software installation and upgrade process. Stay in constant contact with key members of your team.
- Bring in help if you need it. If you have an
IT department, great. Your developers and techs may be able to handle
software installation and upgrade process with relative ease. However, if you don’t, consider outsourcing integration and coordination with an IT services firm. Your outsourced IT can handle everything from server installation to operating system upgrades, according to Geeks On Site. - Document everything. Even if your new software
isn’t particularly complex, still, document your internal processes.
This way, things run smoothly, even without your primary end-user.
- Always test before a full rollout. Don't make this a complicated process. If nothing else, bring in a group of employees on a Saturday for a mock workday to make sure that your new program runs at opening on Monday.
- Get feedback. Finally, no matter the success of your software installation and upgrade process, always ask those who use the program. Don’t just assume that because things went well on test day that these results translated into a seamless user experience. Make sure to ask lots of questions and make changes, if necessary.
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
Adding new and upgraded software to your business is crucial to your success. But don't always “set it and forget it.” Make sure you know how, exactly, to implement a software rollout so that the investment doesn’t slow your company down.
Article written by Cody McBride of techdeck.info for Quality Assurance Solutions. Article edited and posted by Quality Assurance Solutions
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |