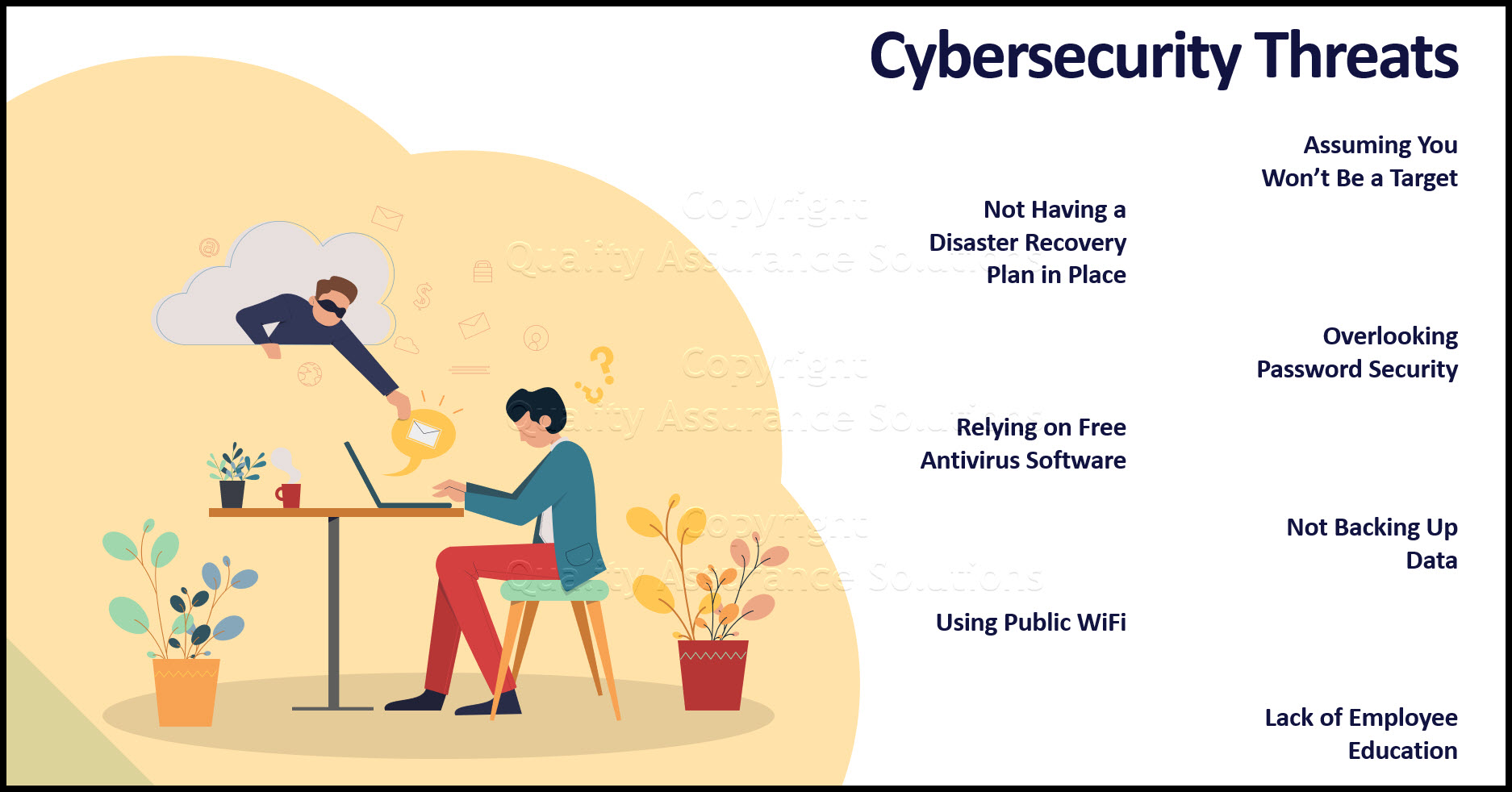
7 Biggest Cybersecurity Threats
These 7 biggest cybersecurity threats make small businesses to mid-size enterprises vulnerable
to cyberattacks. With countless business transactions taking
place online every day, cybersecurity is a growing concern for many companies. If you run a business, you’re probably wondering what you can
do to protect your data and how you can address any mistakes you’re making.

1) Assuming You Won’t Be a Target
For the biggest cybersecurity threats of the 7, business owners simple assume that their company won’t be a target. But even small businesses can become victims of cyberattacks. Whether you have five employees or 500, you need to prioritize cybersecurity measures. Even if you’re a sole proprietor, you need to think about cybersecurity!
TrainingKeeper Software. Keep, organize and plan all your employees' training and activities. Software includes multi-user support with reports, certs, and calendars.
2) Not Having a Disaster Recovery Plan in Place
If your company recently shifted to remote work, you might overlook the fact that your staff might not maintain the same security functions on their personal tech that you installed on your office computers. Basically, remote work without these security features can leave your company vulnerable to cyberattacks. Without proper security measures, your business could be targeted with viruses that delete essential programs or data, spyware that shares sensitive information, or keyloggers that track your employees’ keystrokes.
In the event that the worst does happen and one of these biggest cybersecurity threats hits your business, create and keep a disaster recovery plan in place to help you rebound as quickly as possible. With a solid disaster recovery plan in place, Commvault recommends four elements to ensure the plan’s success:
- Prevent (implement layers of infrastructure protection);
- Monitor your environment daily;
- Restore your data (fast restores mean quickly resuming normal business operations to reduce the impact);
- Test your plan
If putting together an effective disaster recovery plan is outside of your wheelhouse, or you don’t have an IT department to implement a plan for you, then connect with a trusted team of professionals who can help you get things back on the right track.
3) Relying on Free Antivirus Software
Perhaps you installed free antivirus software on company computers. This does not provide an adequate form of protection against harmful viruses. Tom’s Guide states that free versions of antivirus software may lack ransomware detection, digital file shredding functionality, and extra browser protections for more secure Internet usage. For strong protection, take the time to shop around and invest in a paid version.
Employee Handbook Kit includes two Employee Handbook templates for Professional & Manufacturing. Includes over 60 policies and benefits templates.
4)
Using
Public WiFi Supports Biggest Cybersecurity Threats
If your employees work remotely, or if you sometimes work in coffee shops or libraries outside of your office, you might occasionally connect to public WiFi. But many people don't realize this risky cybersecurity threat. The Due blog states that when you use public WiFi, hackers can intercept your communications, collect your log-in information, and even get a hold of your email address and corresponding password, giving them access to your inbox. Refrain from using public WiFi for business purposes, and instruct your employees to apply the same caution.
5)
Overlooking
Password Security
Many people use the same passwords, or very similar passwords, for nearly everything. After all, this is very convenient. However, this means that if a cyber attacker obtains a password that you use for one account, they can access other accounts, too. They could potentially gain access to your company’s finances or other confidential information.
Create strong passwords using uppercase and lowercase letters combined with numbers and symbols. You could also purchase password management software for your business that will create and remember complex passwords for you and your employees.
6) Not Backing Up Data
Every business owner knows that backing up data is crucial. That said, you might be tempted to overlook this task, or you might use an insecure cloud storage program to save your data. Both mistakes can be equally costly to your business. So, make sure to add passwords and expiry dates to any files that you have shared in a cloud storage program, and regularly audit your shared files. You should also turn on account alerts, which assures no one tries to access your storage without your permission.
Get certified in Risk Management through our completely on-line training system. Study at your own pace.
7) Lack of Employee Education
Business owners make another mistake by allowing their employees to trying and figuring out cybersecurity on their own. Instead, you need to educate your employees on cybersecurity. You may want to bring in a cybersecurity expert to instruct your employees on best practices for the workplace. Explain which measures your company takes, the importance of these steps, and how employees can keep their data safe.
It’s all too easy to push cybersecurity to the back-burner when running a business. However, failing to prioritize cybersecurity can harm your business in the long run. If you want to keep your data and finances secure, ensuring that you do not make these mistakes makes a great start!
Article written by Cody McBride of techdeck.info for Quality Assurance Solutions. Article edited and posted by Quality Assurance Solutions
|
Quality Assurance Solutions Robert Broughton (805) 419-3344 USA |
 |
|
Software, Videos, Manuals, On-Line Certifications | ||
|
450+ Editable Slides with support links | ||
|
Corrective Action Software | ||
|
Plan and Track Training | ||
|
AQL Inspection Software |
|
Learn and Train TRIZ | ||
|
Editable Template | ||
|
Templates, Guides, QA Manual, Audit Checklists | ||
|
EMS Manual, Procedures, Forms, Examples, Audits, Videos | ||
|
On-Line Accredited Certifications Six Sigma, Risk Management, SCRUM | ||
|
Software, Videos, Manuals, On-Line Certifications |